
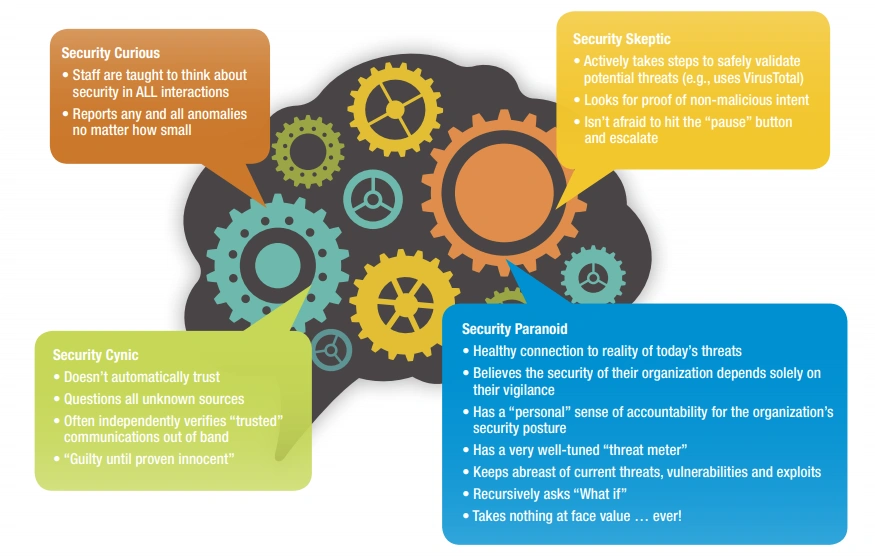
What is Thinking in the Security Context?
One of the biggest challenges organizations face as they strive to safeguard sensitive information is habituating employees to "thinking in the security context." This mindset requires workers to be perpetually cognizant that every task they perform, from Internet downloads to paper recycling, has the potential to create corporate risk exposure if they are not careful.
Which Job Roles Require Security Awareness?
All of them! The level of security awareness naturally varies according to job function, with IT professionals being generally more up to date on the most recent and malicious security threats and internal vulnerabilities, while non-IT staff may be wholly unaware of any risk at all. Cyber criminals rely on ignorance and negligence!
What Factors Inhibit an Employee's Security-Consciousness?
Lack of time/interest/awareness: ordinary job demands, a sense that data security is the domain of the IT department, and an unfamiliarity with the dangers of non-compliance may lead employees to skip time-consuming critical software updates or ignore other security mandates.
False assumptions: uninformed staff may just assume that firewalls will prevent all intrusion, virus scans will avert all dangerous downloads, that data is encrypted, and that hackers aren't targeting their company.
What are Some Common Mistakes that Employees Make?
Without a security-oriented mindset, employees may fail to adequately:
Safeguard passwords: storing, sharing, retaining defaults, rarely updating, and using weak passwords that are easily compromised.
Protect computer privacy: leaving the computer unattended and unlocked, not using a privacy screen in public, not using hibernation settings.
Dispose of sensitive information: recycling documentation that should be shredded, not deleting obsolete files on company hardware, throwing old hardware in the regular trash.
Safeguard data security: connecting via an unsecured wireless network instead of VPN, using unprotected personal devices for work, posting on social media while in the office, using a generic USB drive, leaving sensitive paperwork lying in plain sight or file cabinets unlocked, failing to keep antivirus software current, and worst of all, losing a laptop or other mobile device (the leading root cause of data breach incidents!).

How can Security Risk be Mitigated?
Maintain continual awareness: regularly remind staff about the importance of information security, relay the latest threats, viruses, and infiltration techniques, teach them to spot and avoid vulnerabilities, and instruct them to report suspected breaches/exposure immediately.
Encourage establishment of cautious security practices: emphasize the importance of considered policies related to granting data access and other privileges, sharing proprietary information with vendors and other third parties, and proper disposal of obsolete digital and physical files.
Make security risk relatable: relate common cybercrime tactics by using real-world examples in the business and personal space; it is likely that employees have been, or know people who have been, affected by one of the major data breaches in the past few years or have been the target of social engineering/phishing.
Avoid acronyms and technical jargon: communicate in lay terms as much as possible so that a non-technical audience doesn't tune out.
Emphasize dire consequences to the organization: cybercrime fallout varies according to the size of the breach and the composition and misuse of the stolen data, and ranges from minor inconvenience to financial devastation. Massive data breaches have the potential to cost companies hundreds of millions of dollars in fraudulent charges, debit/credit card reissue, and litigation. Failure to think in the security context can dilute shareholder value and even jeopardize the very survival of the entity.
Learning Tree offers a comprehensive Cyber Security curriculum with learning paths and certifications aligned with the National Initiative for Cybersecurity Education (NICE) framework. Learn more at: LearningTree.com/SecureIT

